Networks and Security
EC3401 - 4th Semester - ECE Dept - 2021 Regulation

2021 regulation - 2nd year, 4th semester paper for ECE Department (Electronics and Communication Engineering Department). Subject Code: EC3401, Subject Name: Networks and Security, Batch: 2021, 2022, 2023, 2024. Institute: Anna University Affiliated Engineering College, TamilNadu. This page has Networks and Security study material, notes, semester question paper pdf download, important questions, lecture notes.
PDF Download Links
Networks and Security
Notes and Question Answer of Unit I: Network Models and Datalink Layer will Uploaded shortly...
Notes and Question Answer of Unit II: Network Layer Protocols will Uploaded shortly...
Notes and Question Answer of Unit III: Transport and Application Layers will Uploaded shortly...
Notes and Question Answer of Unit IV: Network Security will Uploaded shortly...
Notes and Question Answer of Unit V: Hardware Security will Uploaded shortly...
PDF Download Links
Networks and Security
Unit I: Network Models and Datalink Layer
Notes and Question Answer of Unit I: Network Models and Datalink Layer will Uploaded shortly...
Unit II: Network Layer Protocols
Notes and Question Answer of Unit II: Network Layer Protocols will Uploaded shortly...
Unit III: Transport and Application Layers
Notes and Question Answer of Unit III: Transport and Application Layers will Uploaded shortly...
Unit IV: Network Security
Notes and Question Answer of Unit IV: Network Security will Uploaded shortly...
Unit V: Hardware Security
Notes and Question Answer of Unit V: Hardware Security will Uploaded shortly...
PDF Download Links



EC3401
NETWORKS AND SECURITY
COURSE OBJECTIVES:
i. To learn the Network Models and datalink
layer functions.
ii. To understand routing in the Network
Layer.
iii. To explore methods of communication
and congestion control by the Transport Layer.
iv. To study the Network Security Mechanisms.
v. To learn various hardware security
attacks and their countermeasures.
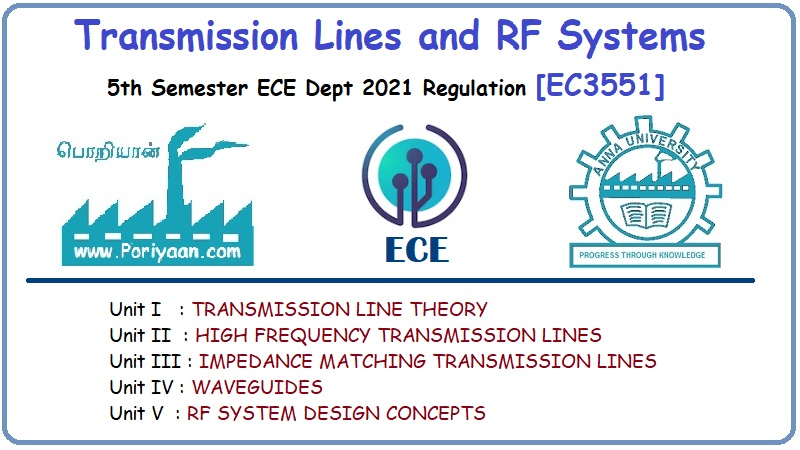
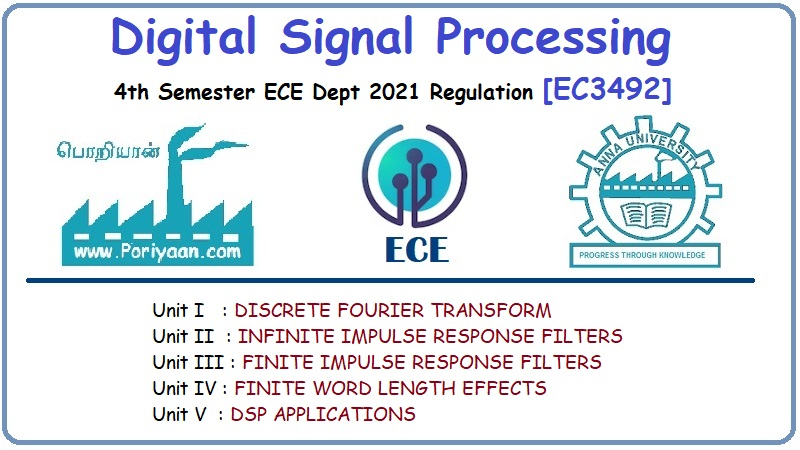
UNIT I
NETWORK MODELS AND DATALINK LAYER
Overview of Networks and its
Attributes – Network Models – OSI, TCP/IP, Addressing – Introduction to
Datalink Layer – Error Detection and Correction – Ethernet(802.3)- Wireless LAN
– IEEE 802.11, Bluetooth – Flow and Error Control Protocols – HDLC – PPP.
UNIT II
NETWORK LAYER PROTOCOLS
Network Layer – IPv4 Addressing –
Network Layer Protocols(IP,ICMP and Mobile IP) Unicast and Multicast Routing –
Intradomain and Interdomain Routing Protocols – IPv6 Addresses – IPv6 – Datagram
Format - Transition from IPv4 to IPv6.
UNIT III
TRANSPORT AND APPLICATION LAYERS
Transport Layer Protocols – UDP and
TCP Connection and State Transition Diagram - Congestion Control and
Avoidance(DEC bit, RED)- QoS - Application Layer Paradigms – Client – Server Programming
– Domain Name System – World Wide Web, HTTP, Electronic Mail.
UNIT IV
NETWORK SECURITY
OSI Security Architecture – Attacks
– Security Services and Mechanisms – Encryption –Advanced Encryption Standard –
Public Key Cryptosystems – RSA Algorithm – Hash Functions – Secure Hash Algorithm
– Digital Signature Algorithm.
UNIT V
HARDWARE SECURITY
Introduction to hardware security,
Hardware Trojans, Side – Channel Attacks – Physical Attacks and Countermeasures
– Design for Security. Introduction to Blockchain Technology.
45
PERIODS
PRACTICAL
EXERCISES: 30 PERIODS
Experiments
using C
i. Implement the Data Link Layer framing
methods,
(a) Bit stuffing, (b) Character stuffing
ii. Implementation of Error Detection
/ Correction Techniques
(a) LRC, (b) CRC, (c) Hamming code
iii. Implementation of Stop and Wait,
and Sliding Window Protocols
iv. Implementation of Go back-N and
Selective Repeat Protocols.
v. Implementation of Distance
Vector Routing algorithm (Routing Information Protocol) (Bellman-Ford).
vi. Implementation of Link State Routing
algorithm (Open Shortest Path First) with 5 nodes (Dijkstra's).
vii. Data encryption and decryption
using Data Encryption Standard algorithm.
viii. Data encryption and decryption
using RSA (Rivest, Shamir and Adleman) algorithm.
ix. Client Server model using FTP protocol.
Experiments
using Tool Command Language
i. Implement and realize the Network
Topology - Star, Bus and Ring using NS2.
ii. Implement and perform the operation
of CSMA/CD and CSMA/CA using NS2.
COURSE OUTCOMES:
Upon successful completion of the
course the student will be able to
CO1:
Explain the Network Models, layers and functions.
CO2:
Categorize and classify the routing protocols.
CO3:
List the functions of the transport and application layer.
CO4:
Evaluate and choose the network security mechanisms.
CO5:
Discuss the hardware security attacks and countermeasures.
TOTAL:75
PERIODS
TEXTBOOKS
i. Behrouz.A.Forouzan, Data Communication
and Networking, Fifth Edition, TMH, 2017.(Unit – I,II,III)
ii. William Stallings, Cryptography
and Network Security, Seventh Edition, Pearson Education, 2017(Unit- IV)
iii. Bhunia Swarup, Hardware Security
–A Hands On Approach,Morgan Kaufmann, First edition, 2018.(Unit – V).
REFERENCES
i. James.F.Kurose and Keith.W.Ross,
Computer Networking – A Top – Down Approach, Sixth Edition, Pearson, 2017.
ii. Doughlas .E.Comer, Computer Networks
and Internets with Internet Applications, Fourth Edition, Pearson Education, 2008.
Networks and Security: Unit I: Network Models and Datalink Layer,, Networks and Security: Unit II: Network Layer Protocols,, Networks and Security: Unit III: Transport and Application Layers,, Networks and Security: Unit IV: Network Security,, Networks and Security: Unit V: Hardware Security,, 4th Semester ECE Dept 2021 Regulation : EC3401 - 4th Semester - ECE Dept - 2021 Regulation Networks and Security